
MOVEit®
Managed File Transfer Software
Progress MOVEit is the leading secure Managed File Transfer (MFT) software used by thousands of organizations around the world to provide complete visibility and control over file transfer activities. Whether deployed as-a-Service, in the Cloud, or on premises, MOVEit enables your organization to meet compliance standards, easily ensure the reliability of core business processes, and secure the transfer of sensitive data between partners, customers, users and systems.

_leader_leaderc3af093e-98f2-4b46-8dc6-630525886b01.png?sfvrsn=b39def32_1)
_momentumleader_leader.png?sfvrsn=9f8929cd_1)
_fastestimplementation_enterprise_golivetime.png?sfvrsn=e81e7f05_1)
_bestestimatedroi_enterprise_roib4336bff-5bf7-433d-bb52-7b046e6b563d.png?sfvrsn=ec1f1864_1)
_bestrelationship_total5dc7bec2-a45e-4dda-8128-246fb082d239.png?sfvrsn=16c13cb7_1)
MOVEit Modules
MOVEit’s flexible architecture makes it easy to choose the exact capabilities that match your organization’s specific needs.

MOVEit Cloud
MOVEit Cloud enables the consolidation of all file transfer activities to one system to ensure better management control over core business processes. A trusted and proven SaaS solution, it provides full security, reliability and compliance with the convenience of a cloud-based service. It provides the security, centralized access controls, file encryption and activity tracking needed to ensure operational reliability and compliance with SLAs, internal governance and regulatory requirements like PCI, HIPAA, CCPA/CPRA and GDPR.

MOVEit Transfer
MOVEit Transfer provides the same award-winning capabilities of MOVEit Cloud in an on-premises solution. Ensure management and control over your business-critical file transfers by consolidating them all on one system. Leverage MOVEit Transfer’s file encryption, security, activity tracking tamper-evident logging, and centralized access controls to meet your operational requirements. Reliably and easily comply with SLAs, internal governance requirements and regulations like PCI, HIPAA, CCPA/CPRA and GDPR.

MOVEit Automation
MOVEit Automation works with MOVEit Cloud, MOVEit Transfer to let admins and authorized users easily create file-based tasks without programming. It automates and controls access to file transfer resources, minimizes workloads and reduces errors while mitigating the risk of data loss. You get a reliable, secure means of sharing business data with an audit trail and visibility into all file transfer activities.
Email and Web Transfer
MOVEit Ad-Hoc makes secure file transfer easily accessible from Microsoft Outlook or a web browser to assure the compliant ad-hoc transfers of sensitive data.
Mobile Managed File Transfer
The free MOVEit Mobile app puts secure and managed file transfer control at your fingertips via your iOS or Android device.
Mulesoft iPaaS Integration
The MOVEit Mulesoft Connector supports the integration of managed file transfer capabilities with any application supported by Mulesoft’s iPaaS solution.
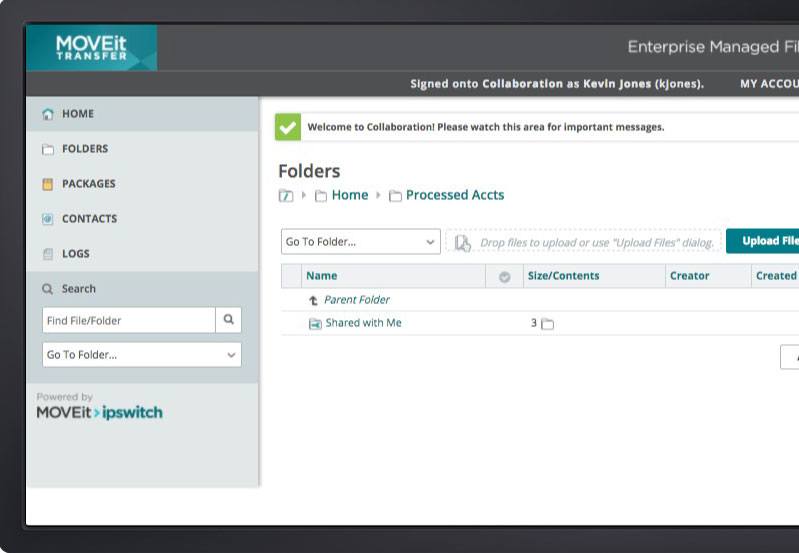
Secure End-User Collaboration
Secure Folder Sharing provides internal and external end users with an easy-to-use, drag-and-drop collaboration capability as an alternative to using email or content collaboration to share sensitive data.
Flexible Deployment
Deployment flexibility means you can meet your exact needs with options ranging from MFT-as-a-Service, to public cloud to on-premises or hybrid cloud solutions.
DMZ Proxy Gateway
MOVEit Gateway is a DMZ proxy server that keeps confidential/sensitive data, authentication, and access information behind the firewall.
Request Pricing
Tell us about your file transfer requirements and get a free no-obligation price quote from one of our experts.
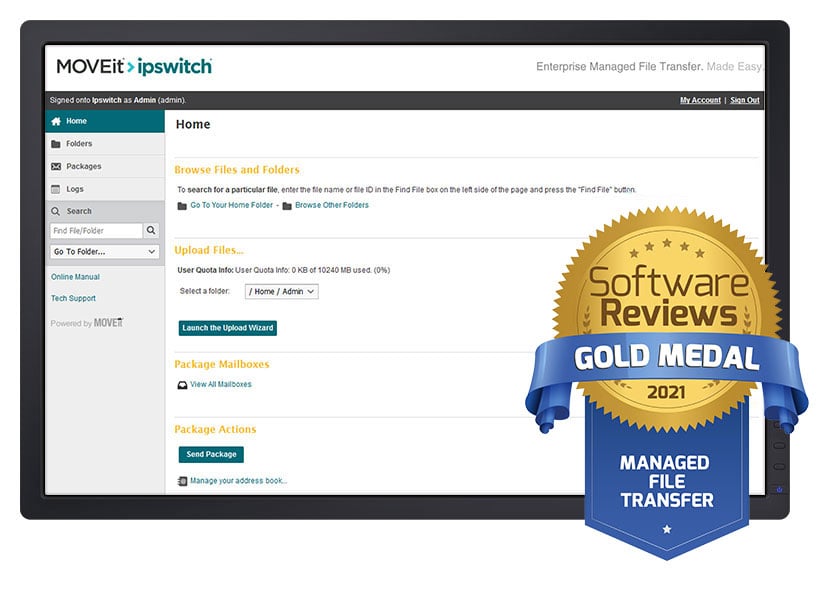
MOVEit Earns Gold Medal in Latest Info-Tech Report
MOVEit named industry leader in latest Info-Tech report on MFT vendors, placing first in quality and breadth of features.
Read the Report >Additional Capabilities
Multi-Tenancy
Our Multi-tenancy option enables MOVEit Transfer to simultaneously serve multiple client organizations, or “tenants”, on a domain or username basis.
High Availability
MOVEit Transfer has a flexible architecture that can be deployed on one or more systems to address availability, performance or scalability requirements.
Desktop Clients
Choose from a full range of desktop clients to meet your needs, including an easy-to-use MOVEit Client for Windows and MacOS, WS_FTP, MOVEit EZ and MOVEit Freely.
API
The MOVEit API offers third-party programs access to a wide variety of MOVEit Cloud and MOVEit Transfer services and administrative capabilities.
MOVEit's Architecture


Start Your Free Trial of MOVEit
Featured Content
MOVEit Managed File Transfer FAQs
What is Managed File Transfer?
A Managed File Transfer (MFT) solution provides the security, visibility, and control required for high-volume, secure file transfers. MFT can assure the reliability of core business processes through the secure and compliant transfer of sensitive data among employees, partners, and customers.
Is MOVEit considered an enterprise-level Managed File Transfer solution?
MOVEit is an enterprise-level MFT with the scalability, secure encryption, and automation capabilities to meet the needs of virtually any size organization.
Which platforms can MOVEit install to?
MOVEit is a purpose-built Windows Server application that can run on-premises or in Azure. MOVEit is also available as a Service, hosted by Progress in the Azure Cloud.
Can MOVEit run in a VMware or other virtual environments?
MOVEit Transfer can be installed and run in virtual environments including:
- VMware ESX (64-bit guest servers)
- Microsoft Hyper-V (64-bit guest servers)
What kinds of MOVEit clients are available?
Mac & Windows Desktop Client
This easy-to-use, drag and drop tool makes it easy for end-users to share files, internally or externally, with the full security, tracking and logging of a MOVEit file transfer. Supported on both Windows and MacOS platforms and built using the MOVEit REST API, this new client can broaden adoption of MOVEit across your end-user base without any training required.
MOVEit Add-in for Outlook
Within Outlook clients on Windows, Mac, or Outlook on the web, send secure files, view read statuses, recall files, and receive secure files without leaving Outlook. Offers improved experience, functionality, and ease of deployment, with no client software for users to install or maintain.
Mobile Client
The free MOVEit Mobile 2.0 app makes it simple to upload, download and manage secure file transfers with your mobile device while enjoying advanced features like Multi-Factor Authentication (MFA) and Secure Folder Sharing. MOVEit Mobile is available for iOS and Android.
Automated & Scheduled Transfer Client
MOVEit EZ is a unique secure transfer client that moves files on a scheduled, automated, firewall-friendly basis between Microsoft Windows 7, 8.1 and 10 desktops and a MOVEit Transfer server, with minimal user involvement.
Command Line
MOVEit Freely is a free command line FTP/secure FTP SSL (FTPS) client for Windows 7, 8, and 10 systems. MOVEit Freely can safely exchange files with secure FTP servers that support 128-bit key SSL (Secure Socket Layer) encrypted transfers, the highest level of protection currently available for Internet communications. MOVEit Freely was one of the first clients to support all three FTP over SSL modes (TLS-P, TLS-C, and IMPLICIT).
Which protocols does MOVEit support?
MOVEit supports the following file transfer protocols.
- FTP
- SSL/FTPS
- SSH/SFTP
- HTTP/S
- SMTP/POP3
- CIFS/SMB (Accessing Network Storage)
- EDIINT AS1, AS2, & AS3
Do my trading partners need any special software to connect to MOVEit?
No special software is needed to connect to MOVEit.
Can my trading partners or employees connect through their browser?
Yes. When an email arrives notifying a recipient of a new MOVEit secure file, the user need only click the link to MOVEit Transfer or copy the link and paste it into their browser. The Sign-on page opens. The Username field contains the recipient’s email address. In the Password field, type the password is then entered that was received in either the package notification email, or in a separate notification email. The user may then click Sign On and the packages from the sender page opens. The recipient may then go to View Packages to see the securely shared files.
Can MOVEit connect to secure FTP servers?
MOVEit Freely can connect to any FTP Server. MOVEit Freely can safely exchange files with secure FTP servers that support 128-bit key SSL (Secure Socket Layer) encrypted transfers, the highest level of protection currently available for Internet communications.
Which database servers can MOVEit connect to?
MOVEit Transfer requires one of the following database platforms:
- MySQL 8 (included in the MOVEit Transfer installation)
- Azure SQL Database
- Microsoft SQL Server 2019 Enterprise/Standard
- Microsoft SQL Server 2017 Enterprise/Standard
- Microsoft SQL Server 2016 Enterprise/Standard
Which file formats does MOVEit support?
MOVEit supports the transfer of any file type.
Does MOVEit need to be installed onto each server it connects to?
MOVEit need only be installed on a single Windows Server or Azure instance. It does not require installation on any other server or endpoint to enable secure file transfer. Remote access to a MOVEit Transfer server is available through a variety of clients.
Is there a free trial available?
Yes! Visit this Progress MOVEit page to start your free trial.
What is MOVEit?
Progress MOVEit is a secure managed file transfer application. MOVEit encrypts data at rest and in motion and provides IT security controls for sensitive business data. With tamper-evident audit logging, multi-factor authentication, and enterprise-grade tools for collaboration, MOVEit is an essential ingredient in meeting HIPAA, GDPR, and ISO 27001 compliance. MOVEit mitigates risks from human error and decentralized “Shadow IT” file transfers.
What are the support hours for Progress MOVEit?
Check out our MOVEit Customer Support Guide page for all of our available tech support options, or read our detailed guide to phone support here.
On which platforms can MOVEit be installed?
MOVEit Transfer server can be installed on Windows Server 2022, Windows Server 2019, or Windows Server 2016. MOVEit Transfer requires .NET 4.7.2. If the server does not have Internet access, you must install .NET by other means before you run the MOVEit Transfer installation program. Windows Server 2019 comes with .NET 4.7.2.
Can you provide me with reference accounts?
Yes! Explore MOVEit use cases on the Progress Resource center.
Do you offer professional services for MOVEit products?
Learn more about available professional services for MOVEit on our Technical Services page.
Can MOVEit automate file exchange with secure FTP servers?
MOVEit Automation works with MOVEit Cloud, MOVEit Transfer, hybrid cloud endpoints (AWS S3, Azure Blob, SharePoint, etc.) or any FTP system to provide advanced workflow automation capabilities without the need for scripting. MOVEit Automation accelerates the rollout of new services and the onboarding of new external data sharing partners by reducing development time while significantly reducing the likelihood of errors.




_leader_leaderc3af093e-98f2-4b46-8dc6-630525886b01.png?sfvrsn=b39def32_1/%0Amanagedfiletransfer(mft)_leader_leaderc3af093e-98f2-4b46-8dc6-630525886b01%0A.png)
_leader_americas_leader.png?sfvrsn=996d76dc_2/%0Amanagedfiletransfer(mft)_leader_americas_leader.png)
_leader_asia_leader.png?sfvrsn=cb711c29_2/%0Amanagedfiletransfer(mft)_leader_asia_leader.png)
_leader_asiapacific_leader.png?sfvrsn=e2168350_2/%0Amanagedfiletransfer(mft)_leader_asiapacific_leader.png)
_leader_emea_leader.png?sfvrsn=1c8b8f2_2/%0Amanagedfiletransfer(mft)_leader_emea_leader.png)
_bestestimatedroi_enterprise_roib4336bff-5bf7-433d-bb52-7b046e6b563d.png?sfvrsn=ec1f1864_1/%0Amanagedfiletransfer(mft)_bestestimatedroi_enterprise_roib4336bff-5bf7-433d-bb52-7b046e6b563d.png)
_bestrelationship_total5dc7bec2-a45e-4dda-8128-246fb082d239.png?sfvrsn=16c13cb7_1/%0Amanagedfiletransfer(mft)_bestrelationship_total5dc7bec2-a45e-4dda-8128-246fb082d239.png)
_bestresults_mid-market_total.png?sfvrsn=c6a6f283_1/%0Amanagedfiletransfer(mft)_bestresults_mid-market_total.png)
_bestusability_enterprise_total7ef87180-cbfa-4ad0-aa5f-4c6dae1c56c3.png?sfvrsn=421d0ed1_1/%0Amanagedfiletransfer(mft)_bestusability_enterprise_total7ef87180-cbfa-4ad0-aa5f-4c6dae1c56c3.png)
_fastestimplementation_enterprise_golivetime.png?sfvrsn=e81e7f05_1/%0Amanagedfiletransfer(mft)_fastestimplementation_enterprise_golivetime.png)
_momentumleader_leader.png?sfvrsn=9f8929cd_1/%0Amanagedfiletransfer(mft)_momentumleader_leader.png)
_mostimplementable_enterprise_total85d23586-25a2-4fc7-b4a3-81f5a836cb59.png?sfvrsn=21bc6210_1/%0Amanagedfiletransfer(mft)_mostimplementable_enterprise_total85d23586-25a2-4fc7-b4a3-81f5a836cb59.png)
_leader_leader.png?sfvrsn=8f9063b2_3)
_bestusability_enterprise_total.png?sfvrsn=1af82ed8_3)
_bestrelationship_total.png?sfvrsn=d09d59c_3)
_bestestimatedroi_enterprise_roi.png?sfvrsn=f5094b80_3)
_mostimplementable_enterprise_total.png?sfvrsn=1245b988_3)





_bestrelationship_mid-market_total.png?sfvrsn=218a8c49_3)






















